Jun 062011
You probably already know or heard me saying “I do not recommend doing this!“. At least Do not do it if you are not sure your machine is safe. Even a friend of yours can get drunk and make you a bad prank if he knows he can sudo in your machine and remove your root directory. It takes a single command.
sudo rm -rf /
If you still need to make passwordless sudo for some reason, there are few things you must set.
Create a user if you don’t have it yet. It takes pressing [enter] about 10 times. Choose a good password. It is important. This user will be able to wreak havoc in your machine.
bash-4.1# adduser baduser
Login name for new user: baduser
User ID ('UID') [ defaults to next available ]:
Initial group [ users ]:
...
...
...
Changing password for baduser
Enter the new password (minimum of 5 characters)
Please use a combination of upper and lower case letters and numbers.
New password: AhBlahBlah123456
Re-enter new password: AhBlahBlah123456
passwd: password changed.
Account setup complete.
bash-4.1#
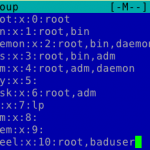
- Add him to group wheel
- Passwordless sudo
Edit /etc/sudoers and /etc/group. Add this bad user to group wheel and uncomment the unsafe passwordless sudo in the sudoers. There. You are set. Let’s try if it works:
baduser@sandbox:~$ sudo touch /etc/test.txt baduser@sandbox:~$ sudo echo "Machine exploited by baduser" > /etc/test.txt
2 Responses to “How to make passwordless sudo in Slackware.”
Sorry, the comment form is closed at this time.
how about not letting the baduser use any command he wants?
in my case the samba guys closed some security hole by not allowing their binaries to run with setuid to root. so now I can’t mount my samba shares. well… I can:
root@cristi:/etc# cat sudoers
# sudoers file.
#
# This file MUST be edited with the 'visudo' command as root.
#
# See the sudoers man page for the details on how to write a sudoers file.
#
# Host alias specification
# User alias specification
# Cmnd alias specification
Cmnd_Alias SMB = /usr/sbin/mount.cifs, /usr/sbin/umount.cifs
# Defaults specification
# Runas alias specification
# User privilege specification
root ALL=(ALL) ALL
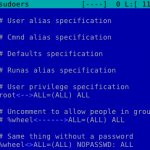
# Uncomment to allow people in group wheel to run all commands
# %wheel ALL=(ALL) ALL
# Same thing without a password
# %wheel ALL=(ALL) NOPASSWD: ALL
# Samples
# %users ALL=/sbin/mount /cdrom,/sbin/umount /cdrom
# %users localhost=/sbin/shutdown -h now
sonty ALL=(ALL) NOPASSWD: SMB
cristic ALL=(ALL) NOPASSWD: SMB
Yeah. This will be very helpful if we need to give explicit mount rights for the user but nothing else.
Thanx alot.